============================================
Introduction: Why API Security is Critical in Perpetual Futures Trading
Perpetual futures trading is one of the most dynamic areas in the cryptocurrency derivatives market. With its 24⁄7 trading cycles, high leverage, and reliance on APIs for automation, it has become a core strategy for both professional and retail traders. However, this dependency on APIs also introduces new risks, making API security solutions for perpetual futures a top priority.
From protecting API keys to preventing unauthorized trades, robust security strategies not only safeguard capital but also ensure compliance with industry standards. This article will provide a deep dive into API security solutions tailored for perpetual futures, explore different strategies, compare their strengths and weaknesses, and highlight best practices based on industry expertise and personal experience.
Understanding Perpetual Futures and API Usage
What are Perpetual Futures?
Perpetual futures are derivative contracts that have no expiry date, unlike traditional futures. They allow traders to speculate on the price of assets such as Bitcoin or Ethereum indefinitely.
Why APIs are Essential for Perpetual Futures
APIs allow traders to automate order placement, risk management, and strategy execution in real time. This is especially important in perpetual futures, where market volatility demands instant decision-making. Many traders ask, “Why API is essential for perpetual futures?” The answer lies in speed, efficiency, and scalability—APIs enable traders to maintain an edge in fast-moving markets.
| Section | Key Points |
|---|---|
| Introduction | APIs essential for automation; security critical to protect capital |
| Perpetual Futures Overview | Derivatives with no expiry, allow indefinite speculation |
| Why APIs Matter | Enable real-time order execution, risk management, strategy automation |
| Common Security Risks | API key theft, MITM attacks, insufficient permissions, bot/DDoS risks |
| Strategy 1: Exchange-Level Security | Use built-in features: IP whitelisting, withdrawal limits, permission keys |
| Exchange-Level Pros | Easy, free, protects against unauthorized withdrawals |
| Exchange-Level Cons | Limited flexibility, varies by platform, insufficient for institutional traders |
| Strategy 2: Custom API Security | Build/integrate layers: encryption, HSMs, access management, MFA |
| Custom Security Pros | Highly customizable, strong key control, supports MFA and biometrics |
| Custom Security Cons | Requires technical skill, higher costs, may add latency |
| Best Strategy | Hybrid model combining exchange-level and custom solutions |
| Practical Solutions | Encrypted key storage, IP whitelisting, permission management, TLS, rate limits, key rotation |
| Secure Automation | Sandbox testing, role-based keys, vulnerability scans, encrypted backups |
| Industry Trends | Zero-trust architecture, decentralized security, AI intrusion detection, institutional MFA |
| Personal Experience | Early unsecured keys caused loss; encryption, whitelisting, monitoring restored safety |
| FAQ 1 | Common mistake: granting full permissions including withdrawals |
| FAQ 2 | Rotate keys every 30–60 days; use automated tools for HFT |
| FAQ 3 | Retail may rely on exchange features; institutions need custom layers |
| FAQ 4 | Monitor API activity with logs/alerts via Splunk or ELK |
| Conclusion | Secure APIs protect funds, strategies, and trading edge; priority for all traders |
1. API Key Theft
If an attacker gains access to a trader’s API key, they can place unauthorized trades, withdraw assets, or disrupt strategies.
2. Man-in-the-Middle (MITM) Attacks
Without proper encryption, API communication between client and exchange can be intercepted.
3. Insufficient Permission Controls
Granting full permissions to an API key unnecessarily exposes trading accounts to risks.
4. Bot Exploitation and DDoS Attacks
Trading bots connected to unsecured APIs may be manipulated to execute harmful trades.
Two Core Strategies for Securing APIs in Perpetual Futures
Strategy 1: Exchange-Level Security Features
Method: Rely on built-in API security measures provided by trading exchanges such as Binance, Bybit, or OKX. These include IP whitelisting, withdrawal restrictions, and permission-based API key creation.
Pros:
- Easy to implement with minimal technical knowledge.
- Often free and integrated into the trading platform.
- Provides essential protection against unauthorized withdrawals.
- Easy to implement with minimal technical knowledge.
Cons:
- Limited flexibility; traders depend on exchange policies.
- Security effectiveness varies across platforms.
- Not sufficient for high-frequency or institutional strategies.
- Limited flexibility; traders depend on exchange policies.
Strategy 2: Custom API Security Solutions
Method: Build or integrate third-party security layers for APIs, including encryption protocols, HSMs (Hardware Security Modules), and custom access management.
Pros:
- Highly customizable for advanced trading needs.
- Provides stronger control over key management.
- Can integrate multi-factor authentication and biometric security.
- Highly customizable for advanced trading needs.
Cons:
- Requires technical expertise or developer support.
- Potentially higher costs for implementation and maintenance.
- May introduce latency if poorly configured.
- Requires technical expertise or developer support.
Which Strategy Works Best?
For retail traders, exchange-level security features often provide sufficient protection. However, institutional traders and algorithmic strategies require custom API solutions for perpetual futures traders to ensure scalability, compliance, and advanced defense mechanisms.
The optimal approach is a hybrid model—leveraging exchange-level features while enhancing them with custom solutions for maximum protection.
Practical API Security Solutions for Perpetual Futures
1. Encrypted API Key Storage
Never store API keys in plaintext. Use AES-256 encryption and secure vaults like HashiCorp Vault or AWS Secrets Manager.
2. IP Whitelisting and Network Segmentation
Limit API access to specific IPs or servers. This reduces the risk of external intrusions.
3. Permission Management
Only grant essential permissions to each API key. For example, create separate keys for order execution and portfolio monitoring.
4. Secure Communication Protocols
Always use HTTPS and TLS 1.3 to prevent MITM attacks during API communication.
5. Rate Limiting and Monitoring
Apply rate limits to prevent bot abuse and monitor unusual traffic patterns in real time.
6. API Key Rotation
Regularly update and rotate API keys to minimize exposure risks.
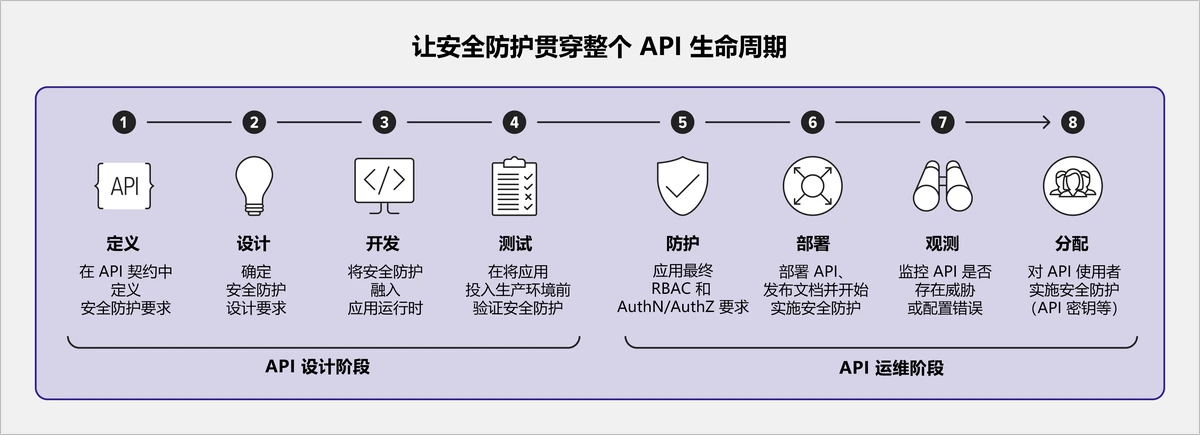
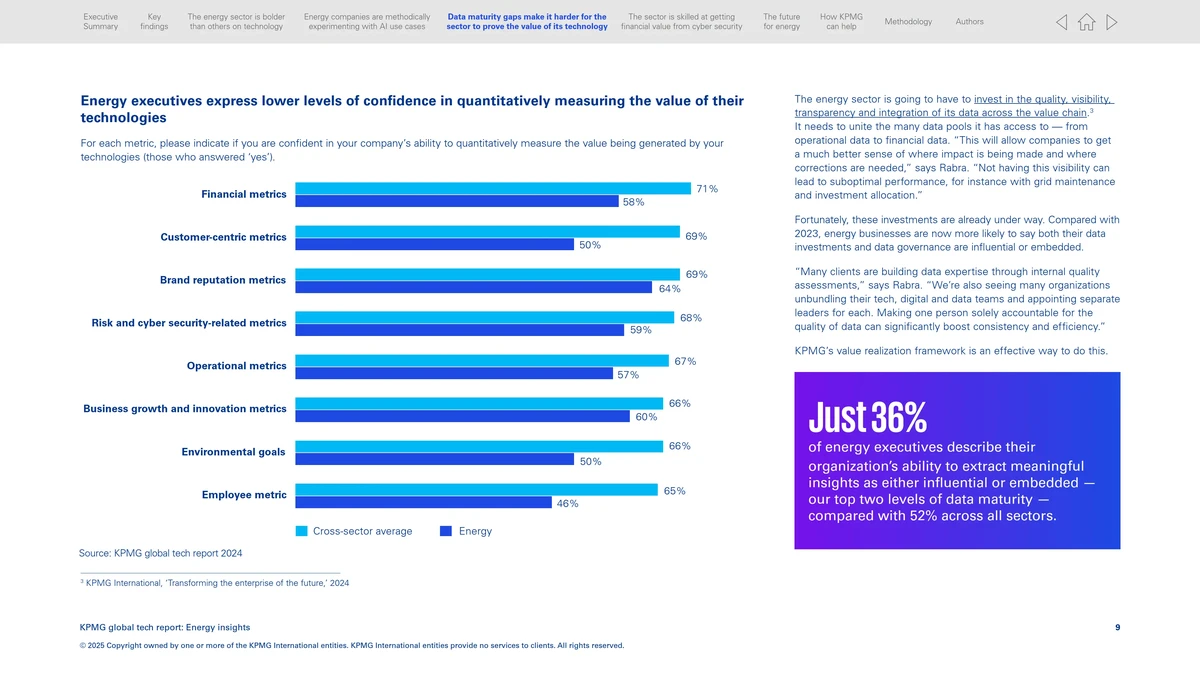
Visual Insights
An overview of API security architecture for perpetual futures.
Example of secure key management for API integrations.
Hybrid model combining exchange-level and custom API security solutions.
How to Automate Trading with Secure APIs
Many traders explore how to automate trading with API for perpetual futures, but automation without security can be catastrophic. Secure automation requires:
- Sandbox testing before deployment.
- Role-based API key separation.
- Regular vulnerability scans of trading bots.
- Encrypted backups of strategies and keys.
Automation should never come at the cost of security—traders must balance efficiency with protection.
Industry Trends in API Security for Perpetual Futures
- Zero-Trust Architecture – No API call is trusted by default; every request is verified.
- Decentralized Security Layers – Use blockchain-based security for decentralized perpetual futures exchanges.
- AI-Powered Intrusion Detection – Machine learning models detect anomalies in API traffic.
- Institutional API Security – Hedge funds are adopting enterprise-level key management solutions with biometric MFA.
Personal Experience with API Security in Perpetual Futures
In my early trading days, I made the mistake of storing API keys directly on a server without proper encryption. Within weeks, unauthorized trades drained part of my margin balance. Since then, I’ve implemented encrypted key storage, IP whitelisting, and monitoring dashboards. The difference has been remarkable—peace of mind and uninterrupted trading.
My advice: Never compromise on API security. Even small traders should treat their APIs with the same caution as their private keys.
FAQ: API Security Solutions for Perpetual Futures
1. What is the most common mistake traders make with API security?
The most common mistake is granting full permissions (including withdrawals) to API keys. Always limit permissions to necessary functions and disable withdrawal access.
2. How often should I rotate my API keys?
Ideally every 30–60 days. Frequent rotation minimizes risks if an API key is accidentally exposed. For high-frequency traders, automated rotation tools are recommended.
3. Can I rely solely on exchange-level security features?
For small-scale retail traders, exchange-level features may be sufficient. However, institutional traders or algorithmic trading strategies require additional layers like encrypted key vaults and intrusion detection systems.
4. How can I monitor unusual API activity?
Use log monitoring tools like Splunk or ELK stack to track unusual API calls, failed logins, or high-frequency requests. Alerts should be automated.
Conclusion: Protecting Your Trading Edge with Secure APIs
Perpetual futures trading offers immense opportunities but comes with significant risks if APIs are not secured properly. By implementing API security solutions for perpetual futures, traders safeguard not only their funds but also their trading strategies and long-term edge.
Whether you are a retail trader relying on exchange-level security or an institutional investor building custom solutions, the priority should always be clear: secure your API before you trade.
👉 What API security strategies have you implemented in your perpetual futures trading? Share your experiences in the comments and help other traders build safer trading systems.